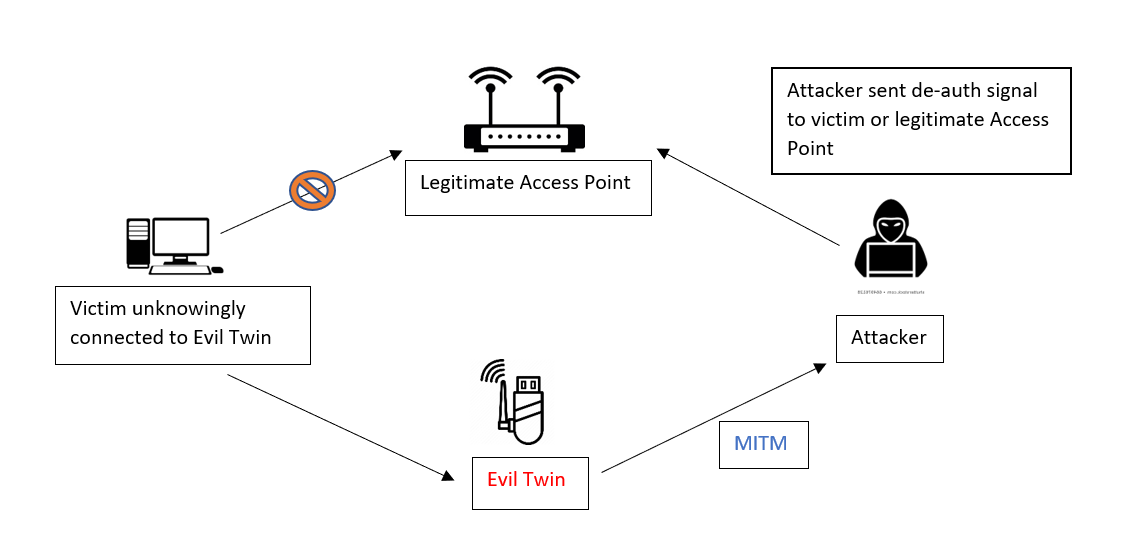
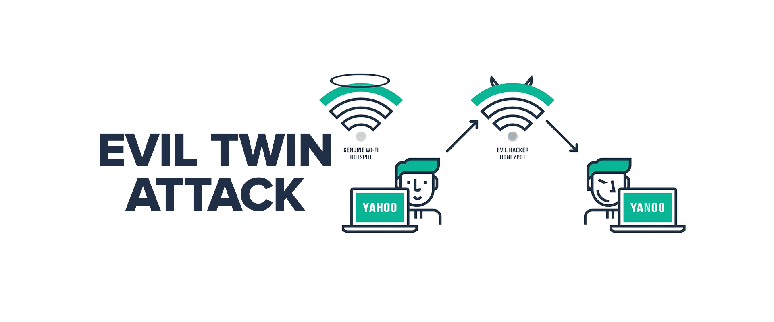
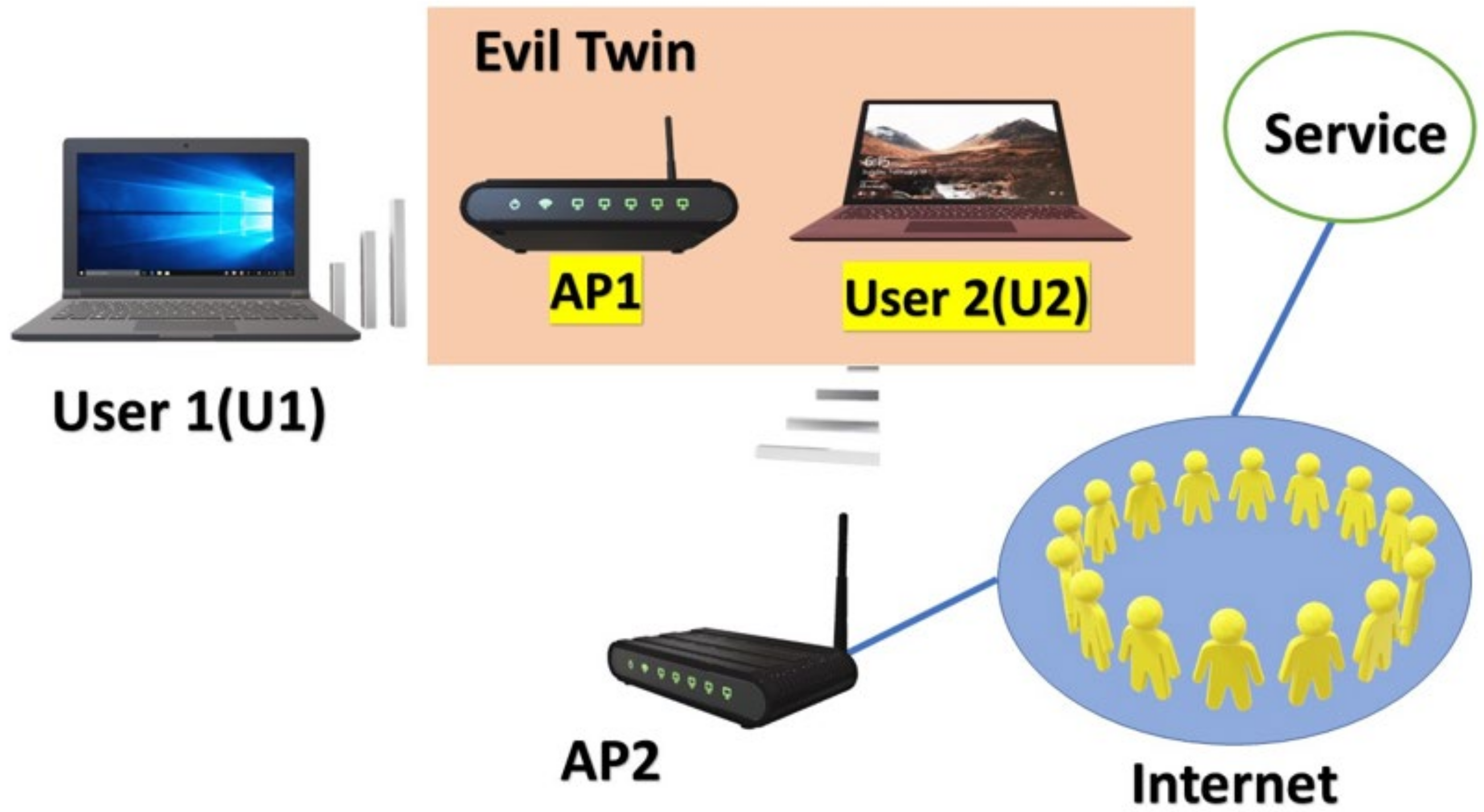
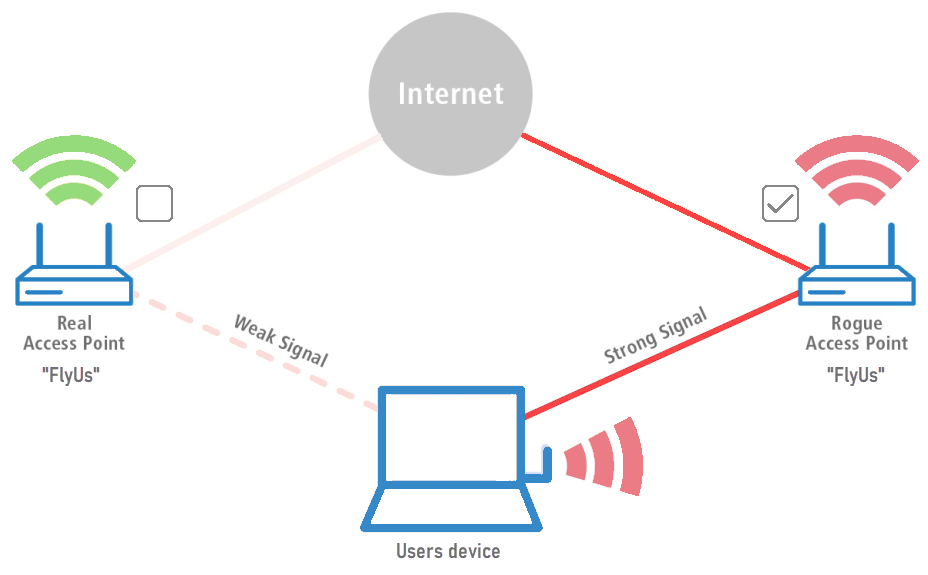
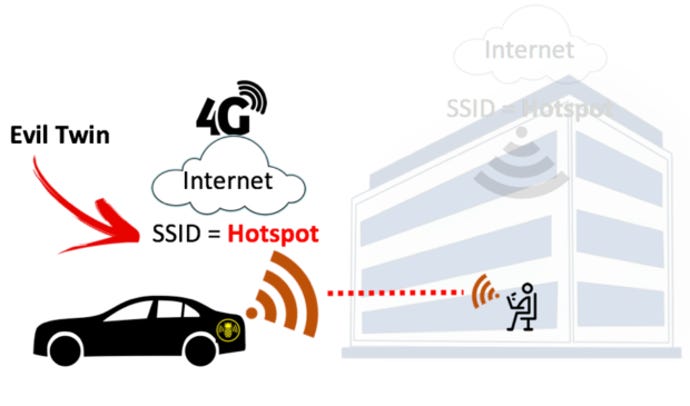
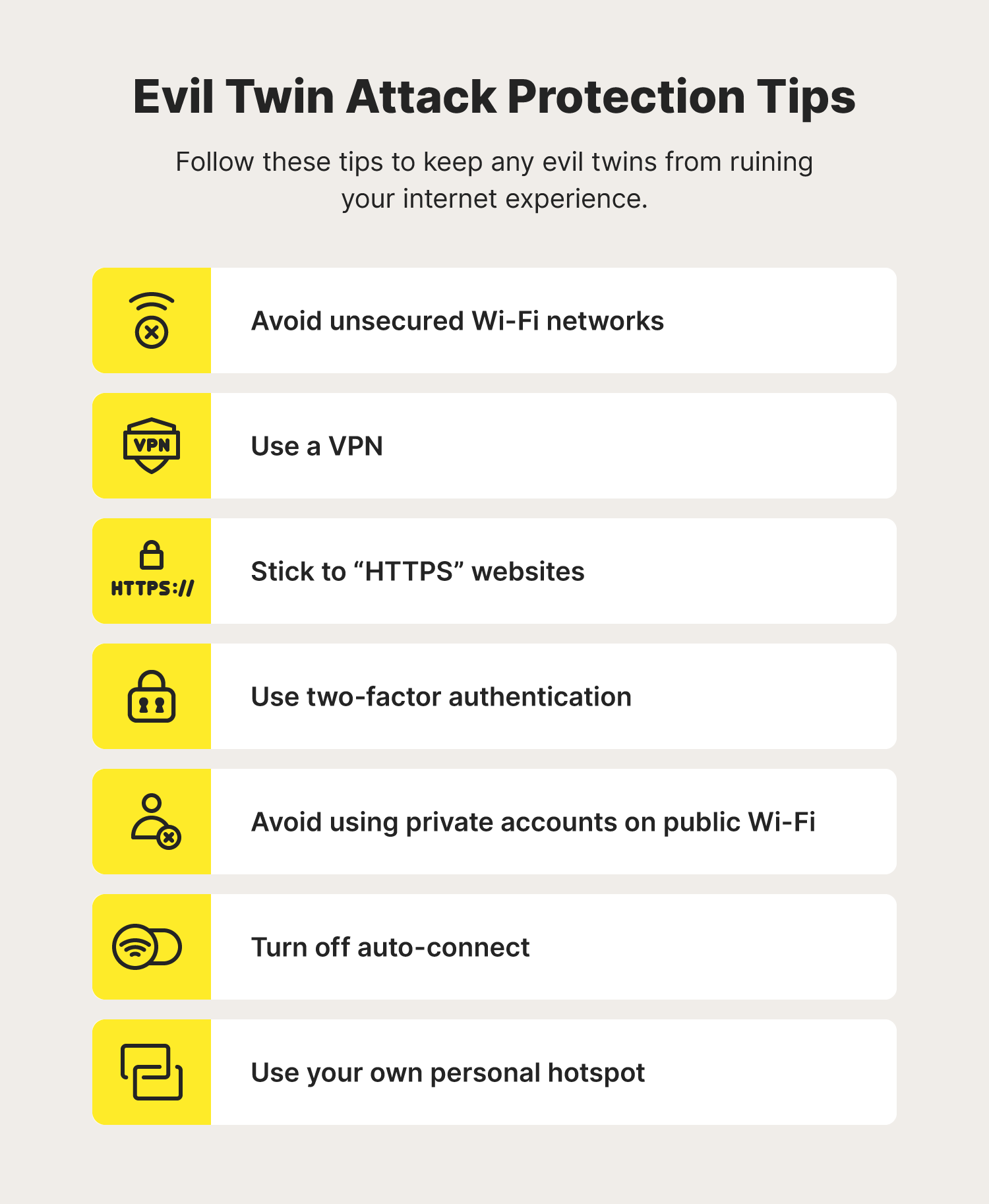
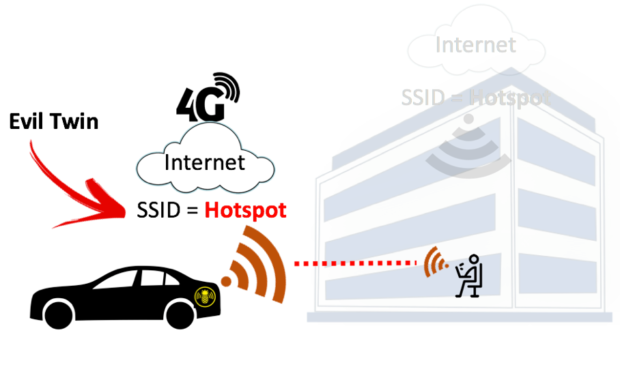
A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library
Wi-Fi CERTIFIED WPA3™ December 2020 update brings new protections against active attacks: Operating Channel Validation and Beacon Protection | Wi-Fi Alliance

Intrusion detection system for detecting wireless attacks in IEEE 802.11 networks - Sethuraman - 2019 - IET Networks - Wiley Online Library

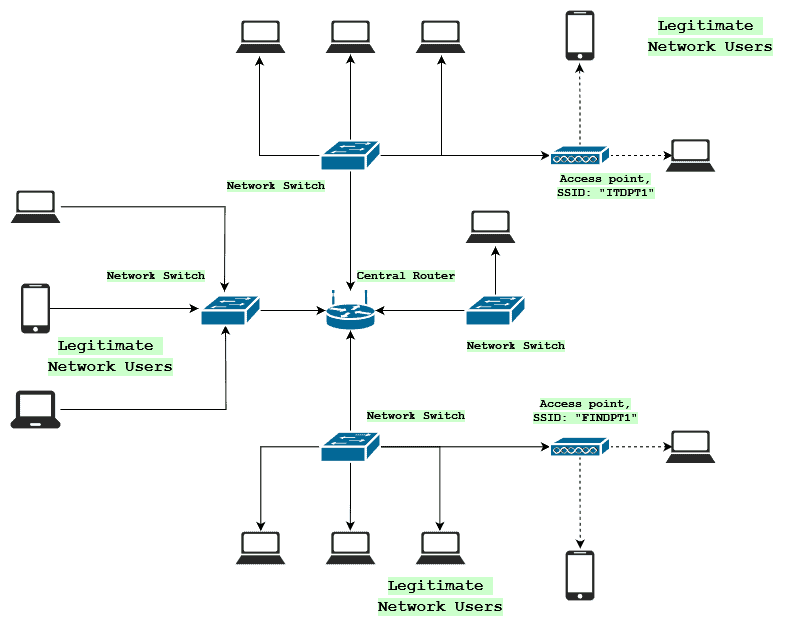
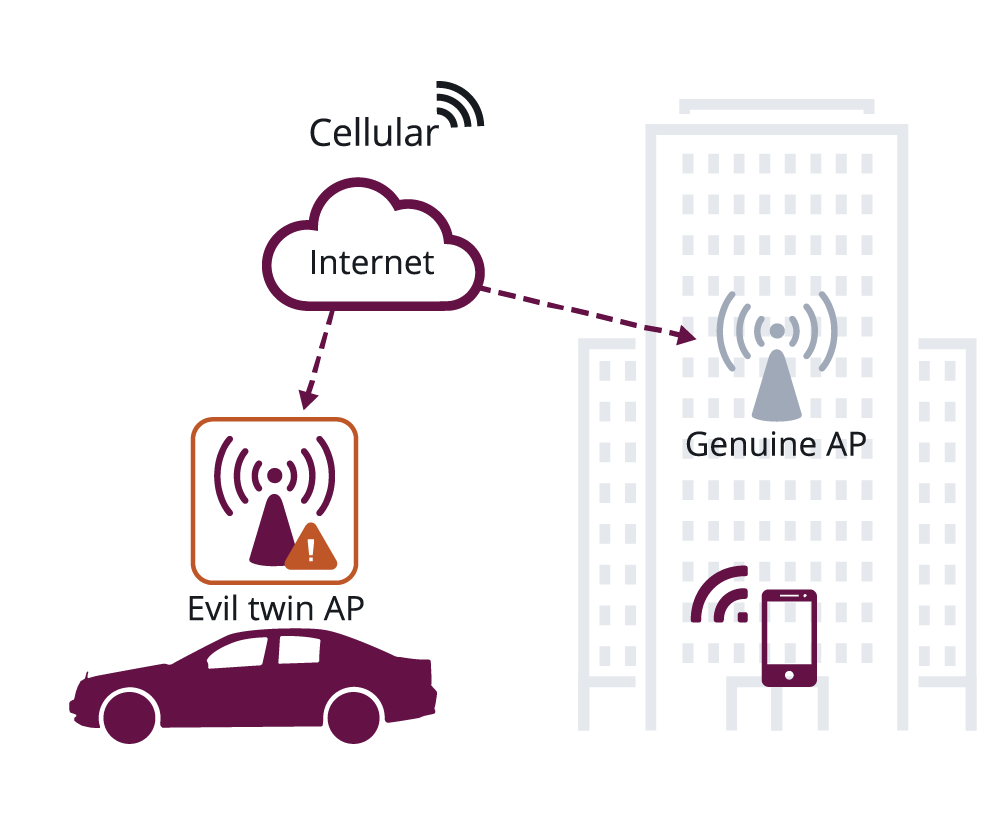
Case 4: Multiple genuine APs and multiple evil twin APs; a sub-set of... | Download Scientific Diagram
![PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man PenTest Edition: Creating an Evil Twin or Fake Access Point on Your Home Network Using Aircrack-ng and Dnsmasq [Part 1 – Setup] – The Cybersecurity Man](https://thecybersecuritymancom.files.wordpress.com/2018/08/evil-twin.png?w=925)